Why Data Matters in 2025
Numbers cut through hype. In 2025, decisions about anonymous networks hinge on evidence, not guesswork. Clear metrics show how people use privacy tools, which services grow, and where risks concentrate. Good data also separates short-term noise from long-term shifts. That matters for users who want safety, for researchers who need signal, and for platforms that must earn trust.
Reliable figures guide product choices. If usage spikes on privacy-first mail or file-sharing, builders invest there. If forums fragment into invite-only spaces, discovery patterns change. Data also exposes weak spots. A rise in phishing clones, for example, tells readers to slow down and verify. The same applies to downtime patterns on hidden services. If outages cluster after takedowns, users learn to expect volatility and plan safer fallbacks.
Metrics also improve education. Articles that cite adoption curves, latency ranges, and survival rates of services teach better than vague claims. With the right charts, a newcomer can grasp why links change, why v3 addresses matter, and why layered security works. Data turns caution from a slogan into a checklist.
Finally, measurement supports accountability. When communities publish update logs, uptime records, and signed notices, trust improves. When they do not, skepticism is healthy. In short, data is the backbone of credible guidance in 2025.
Shifting Landscape of Anonymous Networks
Anonymous networks look very different from five years ago. Access methods have diversified. More people now reach privacy tools through mobile, hardened browsers, and live-boot systems. Bridges and pluggable transports reduce blocking in high-censorship regions. At the same time, communities have moved from open directories to vetted forums and invite-only hubs. That shift reduces exposure but raises the bar for discovery.
Service design has matured. Operators favor minimal attack surfaces, static pages, and split infrastructure. Many publish PGP-signed updates and rotate mirrors with clear procedures. The move from short, weak addresses to longer, cryptographic v3 identifiers is now complete. That upgrade improved authenticity checks and made cloning harder.
Threats evolved too. Scams grew more polished, with convincing UX and recycled brand assets. Drive-by malware remains a real risk, but script-blocking and safer defaults blunt many attempts. Law-enforcement strategy changed as well. Instead of only seizing servers, some teams collect telemetry over time, map relationships, and act when impact is highest.
Discovery patterns continue to shift. Search inside the network favors curated engines that filter known abuse. Forum reputation, cross-signing, and administrator fingerprints now carry more weight than glossy homepages. Users respond by adopting verification habits: compare multiple sources, check signatures, and treat every “new” address as suspect until proven.
The net effect is a tighter, slower, but safer ecosystem for careful users. Impulsive clicks face a higher risk; methodical workflows gain an advantage.
How Trends Influence Privacy, Security, and Policy
Privacy
Trends push privacy in two directions at once. On one side, better defaults help ordinary people stay safer with less effort. Safer browser modes, sandboxed file-views, and stricter permissions reduce mistakes. On the other side, wider mobile use creates fresh leak paths—sensors, app telemetry, and cached media. Users who compartmentalize identities and strip metadata hold the edge.
Security
Operator playbooks now assume volatility. Rotation, redundancy, and signed status pages are standard. Users mirror that mindset with layered access: VPN first when needed, then Tor, then a hardened OS for sensitive tasks. Verification became culture. People check fingerprints, compare mirrors, and avoid downloads unless necessary. These habits cut phishing and reduce supply-chain risk.
Policy
Policy makers read the same usage curves. Where regulators see growth, they debate new controls, from traffic shaping to platform rules. Journalists and civil-society groups respond with evidence on the value of anonymity for speech and safety. That tug-of-war shapes access. Regions with strong digital-rights norms lean toward protecting private browsing. Highly censored regions double down on blocks, which in turn fuels the adoption of bridges and pluggable transports.
For site owners and writers, these trends set the tone. Content that explains risks clearly, cites verifiable methods, and avoids glamorizing crime earns trust with both readers and search engines. For researchers, trend lines reveal where to focus: detection of clones, safer onboarding, and resilient discovery. For everyday users, the lesson is simple. Build habits that scale with change—verify, compartmentalize, and keep tools updated. That approach remains the safest path through an ecosystem that never stops moving.
Key Dark Web Statistics 2025
Global Tor Network Usage and Traffic Volumes
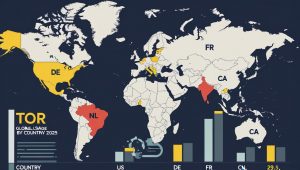
The Tor network remains busy in 2025. Tor’s own metrics list the United States and Germany as the top two sources of directly-connecting clients, with mean daily counts around 1.38M (US) and 0.80M (DE) based on directory-request analysis. These figures come from Tor’s “Users” table, which explains its estimation method and shows the current top-10 countries by relay users. According to public metrics, overall traffic patterns provide insight into both legitimate and malicious activity, as highlighted in Tor Metrics’ official reports.
Onion-service traffic continues to flow at scale. Tor’s onion-service dashboard tracks version 3 rendezvous traffic and provides downloadable CSVs for researchers; the methodology note explains that values are extrapolated from relays acting as rendezvous points. In short: Tor publishes a live, reproducible view of onion-service traffic volumes rather than a single static number.
Academic work helps summarize the magnitude. A 2025 paper in Proceedings on Privacy Enhancing Technologies cites Tor Metrics to report “over 150,000 onion services collectively serve traffic at nearly 4 Gbps,” underscoring that hidden services handle sustained throughput despite volatility. Treat that as an aggregate snapshot rather than a ceiling; load shifts with outages, takedowns, and churn.
Number of Active Onion Services and Growth Rates
Counting onion services is hard because many appear briefly, move, or never advertise publicly. Tor’s “Unique .onion addresses (v3 only)” graph provides the most direct view: it tracks daily unique v3 addresses observed by onion-service directories and offers CSVs plus a technical note on the extrapolation method. This is the authoritative way to discuss growth over time without guessing.
For a broader estimate, a 2025 FOCI/PoPETs workshop paper references a Tor figure of ~800,000 onion services in total, while also noting the limits of collection methods (e.g., services that never publish endpoints). Use this carefully—as an estimate, not a precise count—and pair it with Tor’s live v3 graph when you discuss trends.
User Demographics and Regional Access Patterns
Regional patterns continue to shift with censorship and bridge adoption. Tor’s country table indicates a large share of relay users in the United States, Germany, France, the Netherlands, and Canada, with Russia now lower in the top-10 than in earlier years. These are mean daily client estimates derived from directory requests, and Tor documents the caveats right on the page.
Policy and blocking efforts also influence access. Historical and ongoing reporting shows how national filtering campaigns push users toward bridges and pluggable transports, changing where traffic appears to originate. (Russia’s sustained actions against Tor are a prominent example in recent years.) While these narratives explain why the map changes, Tor’s metrics page remains the primary source for current country-level usage snapshots.
Emerging Trends Across Hidden Networks
Rise of Encrypted Communication Platforms
A clear trend through 2025 is the expansion of privacy-first communication tools within anonymous ecosystems. Onion versions of secure email providers, end-to-end encrypted chat services, and ephemeral file-sharing platforms are becoming primary contact points for activists, journalists, and security-conscious users. Unlike early hidden services, these tools focus less on hosting static pages and more on real-time, secure exchanges.
Several factors drive this shift. First, improved encryption libraries and lighter protocols make encrypted communication easier to run on low-resource servers. Second, users increasingly expect privacy by default rather than as an optional add-on. Finally, geopolitical events continue to push communities toward secure spaces where surveillance pressure is lower. The result is a communications layer inside hidden networks that is both larger and more sophisticated than ever before.
Forum Growth and Private Communities
Forums remain the backbone of most hidden networks, but their character is changing. Open, directory-listed boards are giving way to invitation-only forums, smaller sub-communities, and encrypted group spaces. Operators now prioritize reputation systems, signed announcements, and membership vetting over flashy design. This shift reduces infiltration risks and improves trust signals for regular participants.
The growth of these private hubs reflects broader online behavior. Communities are fragmenting into tighter groups where members know one another, and they rely on shared verification habits such as comparing digital fingerprints or cross-checking mirrors. While this makes forums harder for outsiders to discover, it significantly raises the quality of information exchanged inside.

Marketplace Volatility and Shutdown Patterns
Marketplaces continue to experience frequent disruptions. Voluntary closures, targeted law-enforcement operations, and internal exit scams all contribute to a landscape where stability is rare. In 2025, many marketplaces operate in shorter cycles: they appear, build a small trusted base, and vanish—either deliberately or through pressure.
Operators have adapted by distributing risk. Rather than relying on a single domain, many now rotate multiple mirrors, use signed status pages, and push updates through encrypted forums. Buyers and sellers follow suit by diversifying where they operate, treating every new marketplace as temporary, and verifying announcements before engaging. This constant churn reinforces the need for careful verification and updated intelligence before interacting with any commercial hidden service.
Regional Differences in Access and Use
North America and Europe – Stable but Evolving
In North America and much of Europe, access to anonymous networks remains comparatively stable in 2025. Tor usage has held steady for years in these regions, supported by strong infrastructure, widespread broadband, and fewer direct government blocks. Instead of dramatic surges or drops, the key changes here are in how people connect. More users now rely on privacy-hardened browsers, secure mobile apps, and live-boot operating systems rather than traditional desktop setups.
Legal frameworks also shape usage patterns. Privacy regulations in the EU, like GDPR and ePrivacy, encourage developers to build secure defaults into tools. Meanwhile, debates in the United States over encryption and lawful access periodically flare up, influencing how providers design services. Law enforcement continues to monitor specific cases, but blanket restrictions remain rare. The overall picture is one of steady use, gradual refinement of security habits, and growing public awareness of privacy tools.
Asia and the Middle East – Censorship and Circumvention
Access across Asia and the Middle East tells a different story. Several governments maintain heavy network filtering, targeting anonymity tools with IP blocks, DNS tampering, or deep packet inspection. In response, users increasingly turn to bridges, pluggable transports, and obfuscation protocols to bypass restrictions. Countries such as Iran and China, which have long histories of controlling digital traffic, continue to update their blocking tactics.
This cat-and-mouse dynamic has spurred a rise in regional bridge networks, often maintained by volunteers or small organizations. These bridges help users connect when public relays are inaccessible. In parallel, encrypted messaging apps and onion-enabled mirrors of major news outlets are gaining importance as trusted channels for uncensored information. Usage volumes fluctuate more here than in Europe or North America, but the underlying driver is consistent: censorship pushes innovation in circumvention.
Global Shifts in Anonymity Tools
Beyond regional distinctions, there’s a broader shift toward layered privacy setups worldwide. Users combine multiple tools—VPNs, Tor, hardened browsers, and secure OS environments—to adapt to their local risk environments. Mobile adoption has accelerated, pushing developers to optimize privacy tools for smartphones and tablets without sacrificing anonymity.
Another major shift is the normalization of stronger encryption. The complete transition to v3 onion addresses has improved authenticity checks globally, while new pluggable transports make traffic analysis more difficult. Educational resources and community guides have also improved, meaning more users can configure these tools correctly without expert help. Together, these changes show how access patterns are evolving globally: not only who connects and from where, but how they protect themselves while doing it.
AI and Automation in Monitoring Hidden Services
How AI Enhances Threat Detection
Artificial intelligence has become a powerful force in how security teams, researchers, and even law enforcement monitor hidden services in 2025. Instead of relying solely on manual crawling or static lists, modern monitoring systems use machine learning models to detect patterns of behavior across onion services. These systems analyze link structures, uptime histories, linguistic markers, and transaction metadata (when available) to flag suspicious activity more quickly than human analysts ever could.
One of the most significant advances is in anomaly detection. By training on historical data from marketplaces, forums, and phishing sites, AI tools can identify sudden spikes in malicious hosting, mirrored scams, or bot-driven spam campaigns. They’re also better at recognizing clone sites that imitate well-known services. Subtle differences in layout, text, or cryptographic fingerprints—easy to miss manually—stand out clearly when examined at scale by models trained for that purpose.
Automation has also improved response times. In the past, reports of malicious or fraudulent onion sites often took days to circulate. Now, alerts generated by AI-based scanners can be distributed within hours, enabling researchers and operators to update directories or warn communities before scams spread widely. These tools don’t replace human expertise, but they provide a fast, data-rich foundation for decision-making.
Balancing Privacy and Surveillance in 2025
As AI becomes more embedded in monitoring, the tension between privacy and surveillance grows sharper. On one hand, automated analysis helps detect harmful activities faster, making hidden ecosystems less hospitable to scams, phishing operations, and malware campaigns. On the other hand, widespread data collection—even if focused on metadata and public information—raises legitimate concerns about privacy boundaries.
Privacy advocates emphasize that the same technologies used to find malicious sites could be misused to profile legitimate users or chill free expression. The line between tracking hostile actors and overreaching surveillance depends on established legal frameworks, robust technical safeguards, and effective community oversight. Some privacy-focused projects respond by publishing transparency reports and limiting data retention, ensuring that automated monitoring doesn’t become mass surveillance. This ongoing debate mirrors global privacy discussions documented in Privacy International’s analysis.
By 2025, the debate has matured. Rather than framing AI monitoring as inherently good or bad, communities focus on how it’s implemented. Responsible monitoring emphasizes the use of anonymized data, targeted advertising, and accountability. Poorly governed systems, in contrast, risk undermining the very privacy these networks were built to protect. The balance lies in using AI to improve security without eroding trust—a challenge that shapes both technology and policy in the years ahead.
What These Numbers Mean for Privacy and Security
Implications for Users and Researchers
The statistics and trends emerging in 2025 reveal more than just traffic patterns—they show how behavior and risk evolve together. For individual users, the steady rise in encrypted platforms, private forums, and layered access methods signals a more mature ecosystem. People who adopt strong privacy habits—verifying addresses, using updated tools, compartmentalizing identities—find safer ground than those who treat hidden networks casually. The data confirms that attacks increasingly target careless behaviors, not just technical vulnerabilities.
For researchers, these numbers provide a map of where to focus efforts. Growing activity on invitation-only forums means traditional crawling methods are less effective. Researchers must combine automated discovery with community engagement to track emerging trends accurately. The migration to mobile devices introduces new metadata leak vectors, making device security and app behavior important fields of study. Regional variations also help researchers understand how censorship drives tool adoption, offering real-world insight into the effectiveness of different circumvention techniques. For readers who want to explore safe destinations without falling for clones or scams, our secure onion sites 2025 guide lists trusted platforms that emphasize authenticity and privacy.”
Ultimately, the numbers act as early warning signs. Sharp increases in clone sites, sudden traffic shifts, or unexpected growth in certain regions may indicate either organic expansion or coordinated campaigns. Users and researchers who stay alert to these signals are better equipped to adapt and maintain security.
How Organizations Respond to New Patterns
Organizations—including cybersecurity firms, NGOs, newsrooms, and tech companies—are paying closer attention to trends in hidden services. Rather than viewing these spaces only through the lens of law enforcement, many now approach them as indicators of broader digital change. For example, spikes in whistleblower platform usage can reflect growing political pressure in certain regions, while sudden drops in marketplace activity can foreshadow coordinated takedowns or economic shifts.
Security teams use aggregated statistics to refine monitoring and threat modeling. If traffic to phishing clones grows in a short window, organizations can update detection signatures and warning systems more proactively. NGOs and journalists leverage traffic and service data to understand where anonymity tools are most needed, tailoring support and outreach accordingly. Tech companies, meanwhile, track trends to anticipate how new privacy technologies might affect their infrastructure or user base.
Across the board, the response is becoming more strategic and data-driven. Instead of reacting to isolated incidents, organizations increasingly rely on trend analysis to plan ahead—whether that means reinforcing security measures, supporting privacy initiatives, or contributing to public transparency. In this sense, the numbers don’t just describe the ecosystem; they shape how institutions interact with it.
Final Thoughts – Data Reveals the Real Story
Key Takeaways for 2025
The clearest lesson from 2025’s statistics is that hidden networks are evolving, not disappearing. Traffic volumes remain strong, onion services continue to grow, and usage patterns reflect a maturing privacy ecosystem rather than a fringe space. Encrypted communication platforms are now central, forums have become more selective, and marketplaces operate in shorter, volatile cycles.
Users who take security seriously—by verifying sources, maintaining layered protection, and staying aware of shifting trends—are better positioned to navigate these networks safely. Researchers gain the most value by combining data-driven insights with community understanding, rather than relying on old crawling methods alone. Meanwhile, organizations that monitor these numbers strategically can detect changes early and adapt their policies or protections accordingly.
Overall, the story the data tells is one of increasing complexity paired with stronger defensive practices. The tools are improving, but so are the tactics. Success in this environment depends less on chasing hype and more on understanding the underlying trends.
Why Tracking Trends Will Remain Crucial
Hidden services are dynamic by nature. Addresses change, communities migrate, and technology adapts to both user needs and external pressures. That makes trend tracking an essential skill for anyone serious about privacy, security, or research in 2025 and beyond.
Regularly monitoring usage statistics, service growth rates, and regional access patterns helps users stay a step ahead of potential threats. It also allows policymakers, journalists, and researchers to base their work on verifiable evidence rather than speculation. Trend data highlights emerging risks—like new phishing techniques or sudden network disruptions—before they spread widely.
Just as importantly, tracking trends prevents misunderstandings. Public discourse around the “dark web” often relies on myths or isolated incidents. In contrast, data paints a clearer picture: most activity involves privacy tools, communication platforms, and community spaces—not constant criminality. By continuing to follow the numbers, we can separate fact from fiction, identify real challenges, and make informed decisions in a constantly shifting digital landscape.