🌐 Understanding the Dark Web in 2025
Surface Web, Deep Web, and Dark Web – What’s the Difference?
When people think of the internet, they usually imagine the surface web — familiar sites like Google, YouTube, and Wikipedia that search engines index. But this is only a small fraction of the entire online ecosystem. Beneath the surface lies the deep web, which consists of databases, academic journals, government portals, and personal accounts hidden behind logins. Accessing your online banking dashboard or a private research database falls under the deep web, and none of it is inherently secret or illegal.
The dark web, on the other hand, is a deliberately hidden segment of the deep web that requires special tools such as the Tor Browser or I2P to access. Instead of standard domains like “.com” or “.org,” onion sites often end with “.onion.”They use layers of encryption to protect both the website host and the visitor, making it extremely difficult to trace activity. While some people associate the dark web only with crime, in reality, it also supports journalism, whistleblowing, and private communication. Understanding the difference between these three layers is the first step to seeing the internet in its full context.

Why the Dark Web Exists and What It’s Used For Today
The dark web wasn’t created solely for illegal activity. Its foundation traces back to the 1990s when the U.S. Naval Research Laboratory developed Tor (The Onion Router) to protect intelligence communications. Over time, Tor became open source, allowing anyone to use its anonymity features. This technology gave rise to the hidden network we call the dark web.
In 2025, the dark web serves multiple purposes:
Privacy and anonymity: Individuals use it to avoid mass surveillance or censorship.
Journalism and activism: Whistleblowers and reporters exchange sensitive information without exposing their sources.
Academic and research access: Scholars turn to onion sites to reach materials blocked by paywalls or unavailable in their region.
Digital underground markets: Some marketplaces thrive on anonymity, though they often face law enforcement crackdowns.
At its core, the dark web exists to provide freedom — freedom of speech, freedom from censorship, and freedom from digital tracking. Its uses may vary, but the underlying principle remains the same: protecting privacy in an increasingly monitored world.
Common Misconceptions People Still Believe About Tor Sites
Despite years of awareness, myths about the dark web remain widespread. One misconception is that everything on the dark web is illegal. While it does host criminal activity, many onion sites are legal — including news outlets, secure communication platforms, and non-profit services. Another myth is that just visiting an onion site can get you into trouble. In most countries, accessing the dark web is not a crime; only participating in illegal activities is.
People also assume that the dark web is inherently unsafe and will instantly infect your device with malware. In reality, browsing safely with the Tor Browser, disabling risky scripts, and avoiding suspicious downloads greatly reduces risk. Finally, some believe that using Tor automatically makes you a criminal, but in fact, Tor is used daily by academics, journalists, and even ordinary citizens who value privacy.
By debunking these myths, users gain a more accurate perspective. The dark web is neither a utopia nor a lawless wasteland. It is simply a tool — and like any tool, its impact depends on how people choose to use it.
🔐 How to Access Onion Sites Safely in 2025
Why You Need the Tor Browser (and How It Works)
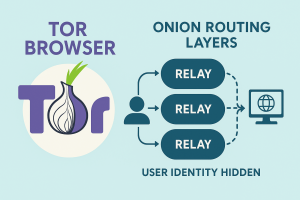
If you want to explore onion sites safely, the Tor Browser is essential. Unlike traditional browsers such as Chrome or Safari, Tor is designed with privacy in mind. It works by routing your traffic through a series of randomly selected servers, known as relays, located across the globe. At each relay, another layer of encryption is removed, similar to peeling an onion. By the time your data reaches its destination, neither the site nor any outside observer can easily trace your activity back to you.
The Tor Project’s guide on how Tor works explains onion routing, which bounces traffic across multiple relays to keep browsing activity private.
This process makes Tor one of the most powerful anonymity tools available to the public. In practice, it means you can visit .onion addresses without exposing your real IP address or physical location. The browser itself also comes with security features, such as blocking tracking scripts and isolating browsing sessions, which further protect users from surveillance and fingerprinting. While some people attempt to reach onion sites using alternative methods, doing so leaves behind digital trails that defeat the purpose of anonymity. For anyone serious about privacy, the Tor Browser is not just recommended — it is the foundation of safe dark web access.
Using a VPN With Tor for Maximum Security
Although Tor provides strong anonymity on its own, pairing it with a Virtual Private Network (VPN) adds another important layer of protection. A VPN encrypts your internet connection before it even enters the Tor network, masking your real IP address from your service provider and making it much harder for anyone to know you are using Tor. This approach is especially helpful in countries where Tor usage is restricted or closely monitored.
Most people use the method often called “Tor over VPN,” which simply means connecting to a VPN first and then opening the Tor Browser. This setup is straightforward and provides an extra shield against unwanted tracking. A more advanced option, known as “VPN over Tor,” sends your data into the Tor network first and then through the VPN. While technically possible, this method is complex and usually unnecessary for everyday users.
Combining a VPN with Tor adds another layer of encryption, but the backbone of Tor itself is onion routing technology, which prevents a single server from seeing both your identity and destination.
The choice of VPN matters as well. Services that operate under strict no-logs policies and are based outside of major surveillance alliances offer stronger privacy guarantees. Combined with Tor, a reliable VPN ensures that your online activity remains both encrypted and anonymous, reducing the chances of exposure through technical flaws or network monitoring.
Device Safety – Antivirus, Firewalls, and Safe Configurations
Even with Tor and a VPN in place, your overall safety depends heavily on the condition of the device you are using. If your computer or phone is poorly protected, malicious actors can still compromise your security. Installing reputable antivirus software is a basic but effective measure, as it helps detect and block harmful downloads or hidden programs that might attempt to run in the background. Keeping this software updated is just as important, since new threats emerge constantly.
A properly configured firewall is another valuable defense. Acting as a gatekeeper, it decides which programs on your device are allowed to connect to the internet. This prevents unauthorized applications from secretly transmitting data, which is a common method hackers use to exploit careless users. Beyond that, good digital hygiene makes a big difference. Keeping your operating system up to date, avoiding unnecessary downloads, and using strong, unique passwords all reduce the chances of compromise. Some privacy advocates even recommend setting up a dedicated device or operating system such as Tails when browsing the dark web, ensuring that personal and anonymous activities remain completely separate.
Ultimately, safe access to hidden services is not just about the tools you use but how you configure and maintain them. Tor and VPN provide anonymity, but without a secure device, your privacy can still be undermined. Taking the time to harden your system creates the final layer of protection that makes responsible dark web exploration possible.
⚖️ Is the Dark Web Legal? Myths vs Reality
What’s Legal vs Illegal on the Dark Web
Many people assume that everything on the dark web is illegal. That’s not true. Accessing Tor sites through the Tor Browser is legal in most countries. Activities such as reading news through a .onion mirror, accessing privacy tools, or using anonymous email services fall under lawful use. In fact, some organizations encourage Tor access to protect free expression and fight censorship.
The illegal side comes down to what you do once you are there. Buying or selling drugs, weapons, stolen data, or counterfeit goods is against the law everywhere. Participating in hacking services, ransomware schemes, or trading child exploitation material is also criminal. Law enforcement agencies across the globe monitor onion networks for these activities and prosecute offenders.
The key point is that the technology itself is neutral. Tor and the dark web can be used for good or bad. Just as a kitchen knife can slice vegetables or cause harm, the dark web’s purpose depends on the user. Understanding this distinction helps break the myth that accessing the dark web automatically makes you a criminal.
Global Laws – How Different Countries Treat Dark Web Access
While Tor and dark web browsing are legal in most regions, different governments approach them in different ways. In the United States and many parts of Europe, simply using the Tor Browser or visiting onion sites is allowed. The law only applies when users cross into illegal activities such as fraud or trafficking. In fact, journalists often rely on Tor to communicate securely with sources without breaking any law.
Some countries, however, see anonymity tools as a threat. China, Iran, and Russia have all restricted or blocked Tor at different times, labeling it as a tool for dissent. In these places, accessing the dark web often requires additional tools like VPNs or bridges to bypass censorship. Using Tor in such regions may not be explicitly illegal, but it can still draw suspicion from authorities and put users at risk. Beyond legality, users often ask about safety, and our article on whether you can get malware by visiting a dark web website explains the risks of even passive browsing.
On the other hand, nations that promote digital freedom—such as Germany, Canada, and the Netherlands—recognize Tor’s role in protecting privacy. They do not criminalize access but still prosecute unlawful transactions. This global mix of tolerance and restriction means that users should always check local laws before exploring. Knowing the legal boundaries is as important as knowing how to use the tools.
The Ethical Side of Exploring Hidden Services
Legality is only part of the equation. Ethics also matter when exploring the dark web. While it may be tempting to view hidden services as mysterious or exciting, responsible browsing means avoiding spaces that exploit others or promote harm. Even if you never buy anything, visiting markets that sell stolen data or counterfeit documents can indirectly support criminal activity.
On the positive side, the dark web can be a force for good. Platforms like SecureDrop allow whistleblowers to share information safely with journalists. News organizations host onion mirrors so people in censored countries can read the truth. Privacy-focused tools help individuals escape surveillance and harassment. These uses show the ethical potential of the hidden internet.
Ultimately, users need to ask themselves why they want to access these services. If the goal is education, research, or privacy, the dark web can be a valuable resource. If the intent leans toward curiosity about illegal markets or hacking services, the risks outweigh the benefits. Ethical exploration ensures that the dark web remains a space that empowers people rather than endangers them.
📚 Types of Onion Sites You Might Encounter
Forums and Anonymous Communities
Forums are the backbone of the dark web. These online communities allow users to exchange knowledge about privacy, security, and underground culture. Some forums are focused on general discussions, while others specialize in topics such as cryptography, operational security, or darknet market reviews. What sets them apart from surface web forums is the high level of anonymity. Members use pseudonyms, and moderators enforce strict rules to keep conversations safe and private.
Well-known platforms such as Dread have been compared to Reddit because of their structure and active participation. Users can ask questions, post guides, and warn others about scams. Smaller boards exist too, offering niche discussions for researchers or people interested in encryption. While some forums touch on illegal subjects, many serve as support hubs for individuals in censored regions who want to share experiences without fear.
For newcomers, forums are often the first stop after installing Tor. They provide a window into how people interact within hidden communities, whether for education, activism, or underground commerce. Their influence on the culture of the dark web is undeniable, and they continue to evolve in 2025.

Privacy Tools and Encrypted Services
One of the most constructive categories of onion sites focuses on privacy tools. These services give users secure communication options and protect sensitive data from prying eyes. The most popular examples are encrypted email platforms such as ProtonMail and Tutanota, both of which offer onion versions to bypass censorship and add another layer of security. Users access these mirrors to keep their conversations private, even in countries where normal access might be blocked.
Beyond email, there are anonymous messaging tools like Ricochet, which operates entirely over the Tor network without needing central servers. This makes surveillance nearly impossible and gives users full control of their conversations. File-sharing tools such as OnionShare also belong here. They allow people to transfer files directly between computers, avoiding cloud services that may log or expose data.
These services highlight the positive side of the dark web. Instead of focusing on crime, they promote digital privacy and personal freedom. They are valuable for activists, journalists, and ordinary citizens who want to take control of their information. As awareness of surveillance grows worldwide, these encrypted services will likely become even more important.
News and Whistleblowing Platforms
Another important group of hidden services exists to protect the free flow of information. Many major news outlets maintain onion mirrors so that readers in censored countries can access content safely. The BBC, The New York Times, and ProPublica are just a few examples. Their Tor versions ensure that government firewalls or monitoring systems cannot block citizens from reaching unbiased reporting.
Whistleblowing platforms also play a critical role. SecureDrop is widely used by journalists to receive confidential documents from sources. It allows whistleblowers to share sensitive information without exposing their identity. Similar platforms, like GlobaLeaks, give NGOs and activists the ability to publish reports and evidence securely.
These services represent the ethical and legal strengths of the dark web. They show how hidden networks can empower people rather than endanger them. For someone living under heavy censorship, accessing these onion sites can mean the difference between staying informed and living in silence. They stand as proof that the dark web has legitimate purposes that go far beyond its criminal reputation.
Marketplaces – Legal and Illegal Sides
Marketplaces are among the most controversial onion services. Some operate legally, offering privacy-friendly services, books, or digital tools. Others exist on the illegal side, selling drugs, counterfeit documents, or stolen data. The rise and fall of these marketplaces is a constant cycle. Law enforcement often shuts them down, only for new ones to appear weeks later under different names.
Not all markets are inherently illegal. For example, certain platforms focus on harm reduction, offering guides, forums, or even products like encryption software. But the majority that gain media attention do so because of their involvement in illicit trade. These sites typically use escrow systems and cryptocurrencies such as Bitcoin or Monero to conduct transactions while attempting to maintain anonymity.
It’s important to recognize that just visiting a market page is not necessarily illegal, but buying or selling prohibited goods is. For beginners exploring the dark web, these markets serve more as a cautionary tale than a recommended destination. They are a reminder that while the dark web can host valuable services, it also provides space for activities that can result in serious legal consequences.
Search Engines for Onion Sites
Marketplaces are among the most controversial parts of the hidden web. The most widely known is the onion version of DuckDuckGo, which allows private searches without logging user activity. Another trusted option is Ahmia, which filters out illegal content and offers a safer way to find legitimate onion services.
Other engines, like Not Evil and Candle, provide broader searches but sometimes include questionable results. Users must double-check links carefully to avoid phishing clones or scam sites that mimic legitimate ones. Search engines on the dark web often rise and fall quickly, with some disappearing without warning.
These platforms are crucial because they give users a way to explore beyond word-of-mouth recommendations or community forums. However, unlike the surface web, there is no perfect search index. That means users need to rely on trusted sources and verify each site they visit. The lesson is clear: even with dark web search engines, skepticism is your best friend.
File Sharing, Libraries, and Research Resources
File-sharing services and digital libraries form another significant category of onion sites. These platforms allow users to exchange files securely and sometimes anonymously. OnionShare, for example, creates temporary servers that enable private file transfers without relying on third-party cloud storage. This is especially useful for journalists, activists, or researchers who need to share sensitive material.
Digital libraries are also common. Projects like Imperial Library of Trantor or mirrors of Sci-Hub provide access to academic papers, books, and other knowledge resources that may be locked behind paywalls on the surface web. While some of these services exist in legal grey areas, others operate with the goal of promoting open access to information.
For students, researchers, and information seekers, these resources are invaluable. They show that the dark web is not only about markets and forums but also about knowledge-sharing and education. By protecting access from censorship and surveillance, these platforms support the idea that information should remain free and available to those who need it.
🕵️♂️ Verified Onion Sites Worth Knowing in 2025
Trusted Search Engines (DuckDuckGo, Ahmia, etc.)
Finding reliable onion sites is difficult without the right tools. Since Google and Bing do not index .onion addresses, users turn to search engines built specifically for hidden networks. The most widely trusted option is the onion version of DuckDuckGo, which works almost the same way as its surface web counterpart. It does not log search activity or store personal information, making it one of the safest entry points for new users.
Another solid option is Ahmia, a search engine that collaborates with the Tor Project. Ahmia filters out illegal content and highlights onion sites with educational or privacy-focused value. This makes it more beginner-friendly and less risky compared to smaller engines that index everything. Other names such as Not Evil or Candle exist, but they often fluctuate in reliability and may show links to harmful sites.
In 2025, these trusted search engines will remain essential for exploring the hidden web. They give users a way to discover services without relying solely on forums or directories, but caution is still important. Even the best search engines cannot stop phishing clones or malicious actors from creating fake sites. That responsibility rests with the user.
Privacy-Focused Communication Tools (ProtonMail, Tutanota, etc.)
One of the strongest positive aspects of the dark web is the rise of privacy-first communication tools. Services like ProtonMail and Tutanota offer onion versions of their email platforms, giving users secure access even in countries where encryption tools face restrictions. These services rely on end-to-end encryption, meaning only the sender and receiver can read the messages.
For users who want something even more anonymous, tools like Ricochet stand out. Instead of routing messages through central servers, Ricochet assigns each user a unique onion address. Conversations take place directly over the Tor network, making surveillance and interception extremely difficult. This approach appeals to activists, journalists, and anyone who wants more control over their digital footprint.
The popularity of these services shows that privacy is no longer a niche interest. In 2025, more people are turning to secure communication as concerns about surveillance grow. Onion-based tools provide a practical solution, proving that the dark web is not only about illegal markets but also about protecting freedom of speech and private conversations.

Media and Journalism Hubs (BBC Tor, ProPublica, SecureDrop)
News organizations were among the first to see the value of onion sites. Outlets like the BBC and ProPublica operate Tor mirrors so readers in restricted regions can access accurate reporting. These mirrors work just like their surface web counterparts but bypass censorship systems. For citizens living under strict regimes, they are sometimes the only way to read uncensored news.
Whistleblowing platforms are also crucial. SecureDrop allows journalists to receive sensitive files securely from anonymous sources. The system runs on Tor and has been adopted by dozens of media outlets worldwide. It protects both whistleblowers and reporters, ensuring that important stories can reach the public without putting sources in danger.
One of the most trusted journalism projects on the dark web is the official BBC Tor mirror, which provides global audiences with uncensored access to news, even in countries where the BBC is blocked.
By combining mainstream journalism with secure communication, these hubs highlight one of the most powerful uses of the dark web. They show that onion services can uphold democratic values and protect the public’s right to information. Instead of being seen only as a place for crime, the dark web becomes a lifeline for truth and accountability.
Academic and Research Access (Sci-Hub, Imperial Library, Archives)
The dark web also plays an unexpected role in education and research. Platforms like Sci-Hub provide access to millions of academic papers that would otherwise be locked behind expensive paywalls. For students and independent researchers, this access levels the playing field, allowing learning without financial barriers.
Other libraries, such as the Imperial Library of Trantor, host vast collections of books ranging from science and history to fiction. These resources are available in regions where physical books are rare or heavily censored. Archives of government documents and leaked files also circulate in hidden communities, offering material for investigative research.
While some of these sites operate in legal grey zones, they highlight the constructive side of the dark web. Instead of focusing only on underground markets, this corner of the onion network promotes knowledge-sharing and educational growth. In 2025, these platforms will remain among the most visited onion services because they provide something universal: access to information.
Other Notable Services (OnionShare, Blockchain explorers, etc.)
Beyond search engines, communication tools, and libraries, other onion services deserve attention. OnionShare is one example. It allows users to host temporary websites, share files, or even run private chat rooms without relying on centralized servers. Once the session ends, the service disappears, leaving no trace. This makes it ideal for journalists, activists, and anyone who values discretion.
Developers and cryptocurrency users also find value in dark web tools. Blockchain explorers with onion versions let people track transactions without exposing their browsing data to public servers. Privacy-focused wallets like Wasabi also offer hidden services, ensuring that financial activity remains anonymous.
These services show the creative ways people adapt the Tor network to everyday needs. Whether it’s sharing documents, running small websites, or managing cryptocurrency, the dark web offers more than people often expect. They prove that innovation and privacy go hand in hand, even in an environment often misunderstood as purely criminal.
💡 How to Spot Fake or Dangerous Onion Links.
Phishing Clones and Scam Markets
One of the biggest risks on the dark web is stumbling onto a phishing clone. These sites look almost identical to trusted platforms, but their purpose is to steal logins, cryptocurrency, or personal information. Scam markets also follow this pattern. They may advertise products or services, but disappear after taking payments. Because onion addresses are long and complex strings of characters, it is easy for criminals to create convincing copies that fool inexperienced users.
To avoid these traps, visitors must be vigilant. Always double-check every character in a URL before entering sensitive details. Even a single typo can lead to a fake site. Many users rely on trusted forums or curated directories that publish verified links. Bookmarking addresses after verifying them also helps prevent mistakes.
Phishing and scam markets thrive on carelessness. Once you know that clones exist, you can develop browsing habits that keep you safe. Treat every new link with suspicion until you have confirmed its legitimacy.
Honeypots – How Law Enforcement Sets Traps
Law enforcement agencies also operate on the dark web. In some cases, they set up honeypots—sites designed to attract criminals and gather evidence. These honeypots may look like marketplaces, forums, or even file-sharing services. Their purpose is not to scam users but to identify illegal activity and build cases against offenders.
For casual visitors, honeypots are rarely a concern. Browsing legal services, such as news sites or privacy tools, does not put you at risk. Problems arise when people engage with markets that promote criminal trade. These spaces are more likely to be monitored, and any interaction could create a legal trail.
The existence of honeypots is a reminder that the dark web is not invisible to authorities. Even though Tor provides anonymity, law enforcement has become skilled at tracking suspicious activity. Staying on the safe side means avoiding illegal platforms altogether. It ensures that your exploration remains both ethical and legal.
Signs of Malicious Onion Addresses
Some onion links reveal their danger before you even click on them. Suspiciously short lifespans, frequent address changes, or lack of references on trusted forums can all point to malicious intent. Many harmful sites push malware downloads, spyware, or ransomware as soon as you open them. Others may overload your browser with scripts designed to weaken Tor’s defenses.
Learning to identify these warning signs is essential. If a site asks for personal details, demands payment up front, or tries to download files automatically, it is likely malicious. Reputable onion services usually appear in discussions among long-standing community members. Scam sites often have no history or vanish without notice.
The safest strategy is to limit your browsing to well-known, verified sources. Treat every new or unknown link with skepticism. By paying attention to small details, you can avoid traps that target the unwary. Over time, recognizing suspicious patterns becomes second nature, making your dark web experience far safer.
🛡️ Dark Web Safety Best Practices for 2025
Identity Protection – Separating Real and Dark Web Personas
The first rule of safe dark web browsing is protecting your identity. Never use your real name, email, or personal accounts on onion services. Once you mix personal data with anonymous browsing, the separation is gone, and so is your privacy. Instead, create a dedicated identity for the dark web. That means a new username, secure password, and, if needed, a fresh email address from a privacy-focused provider.
Using this separate persona reduces the risk of linking your dark web activity to your real-world life. For even greater protection, avoid logging into social networks, banking sites, or work accounts while using Tor. Keep your anonymous identity strictly isolated from personal activities. Think of it as wearing a mask online; once removed, you cannot put it back on.
Security experts warn that scams and malicious markets thrive in hidden networks, and guides like Bitdefender’s What is the Dark Web definition highlight why users should remain cautious even when browsing seemingly harmless onion sites.
In 2025, law enforcement and private trackers will have advanced tools for cross-referencing data. A single slip—like reusing a password—can undo years of careful browsing. Maintaining two completely separate digital lives is the foundation of dark web safety.
Avoiding Malware, Scams, and Phishing Links
The dark web is full of hidden dangers. Malicious links can spread malware that steals files or takes control of your system. Scam markets lure people with promises of rare goods but vanish after taking payments. Phishing clones, which look like trusted services, exist solely to capture login details or cryptocurrency keys.
The safest defense is awareness. Never download random files, and avoid clicking on links you don’t fully trust. Rely on directories or forums that share verified onion addresses. Keep your Tor Browser updated, since new versions patch known vulnerabilities. Consider browsing with scripts disabled, as many attacks rely on JavaScript exploits.
Scammers count on curiosity and haste. Taking a moment to check a site’s reputation before interacting can save you from serious loss. When in doubt, close the page and search for confirmation in trusted communities. By approaching every new link with caution, you drastically reduce the risks of malware or scams. To avoid phishing traps and malicious services, stick to secure onion sites in 2025 that are community-verified and focused on privacy.
Mental Health & Digital Hygiene When Exploring the Dark Web
Dark web browsing comes with more than technical risks. Some sites contain disturbing or violent material that can have a lasting effect on your mental health. Even if you never intend to visit such content, stumbling across it is possible. Preparing yourself mentally and knowing when to disconnect is just as important as configuring your device.
Set clear goals before opening the Tor Browser. If your purpose is research, privacy, or accessing legitimate services, focus only on that. Avoid wandering into unknown territories without reason. Practicing good digital hygiene also helps. Clear your browsing sessions, avoid storing unnecessary files, and never mix personal habits with anonymous activities.
Mental health matters in the digital world. The dark web can feel overwhelming, but stepping back when needed keeps your experience safe. Remember, protecting your mind is part of protecting your privacy. Responsible exploration means knowing your limits as much as knowing the tools.
📈 Tools That Enhance Dark Web Browsing
VPNs and Privacy-Focused Operating Systems (Tails, Qubes, Whonix)
Tor alone gives anonymity, but pairing it with the right tools makes browsing safer. A VPN is the first layer many users add. It hides Tor usage from your internet service provider and creates an extra shield of encryption. In countries where Tor is restricted, a VPN can make the difference between open access and blocked connections. Choosing a provider with a strict no-logs policy is critical.
Beyond VPNs, privacy-focused operating systems provide a safer environment. Tails is one of the best-known. It runs directly from a USB stick and leaves no trace once shut down. This makes it ideal for journalists, researchers, and anyone who wants clean sessions every time. Qubes OS takes a different approach, using virtualization to separate activities into isolated “qubes.” Even if one cube is compromised, the rest remain secure. Whonix integrates directly with Tor and offers strong protection against IP leaks.
These systems go beyond ordinary security software. They create entire environments designed to defend privacy at every step. In 2025, combining Tor with a VPN and one of these operating systems represents one of the strongest setups for safe exploration of the hidden web.
Password Managers and PGP for Secure Communication
Strong passwords are the backbone of online safety, and this holds on the dark web. Many onion services require logins, and reusing the same password is a common mistake. A password manager helps create and store unique credentials for every site. By generating long, random passwords, it removes the human tendency to reuse simple ones. Popular managers like Bitwarden and KeePass also work offline, reducing exposure to online attacks.
For communication, Pretty Good Privacy (PGP) remains a standard. PGP uses public and private key pairs to encrypt messages. Even if someone intercepts the communication, they cannot read it without the matching key. Many journalists and whistleblowing platforms require PGP to verify identities and protect sensitive exchanges. While learning to use PGP takes effort, it offers unmatched security.
Together, password managers and PGP form a strong defense. One protects accounts from brute-force or credential-stuffing attacks, while the other keeps conversations private. For anyone using dark web services regularly, these tools are not optional but essential.
Dark Web Monitoring Services (checking if your data is leaked)
The dark web is notorious for trading stolen credentials and personal data. Entire databases of emails, credit card numbers, and login details appear on underground forums and marketplaces. That is why dark web monitoring services have grown popular. These tools scan hidden networks for signs of your personal information and alert you if it appears.
Services like Have I Been Pwned, while surface-based, track breaches that often originate from the dark web. Premium cybersecurity tools and some VPN providers now offer deeper monitoring, checking onion sites, and leak forums. If your email, phone number, or banking details surface, you receive an immediate warning.
Monitoring services cannot erase stolen data, but they give you the chance to act quickly. Changing passwords, freezing cards, or contacting banks at the right time limits damage. For businesses, these tools also protect brand reputation by catching leaks before criminals exploit them.
In 2025, with data breaches more frequent than ever, ignoring dark web monitoring is risky. Staying proactive ensures that if your details appear in hidden markets, you can respond before the situation escalates.

🔎 Finding Fresh and Active Onion Links
Trusted Directories and Forums for Updated Links
Because onion addresses are long, random, and often temporary, directories remain one of the most useful tools for dark web navigation. Trusted directories collect verified links and update them frequently, giving users a safer way to discover active services. Some directories focus on general categories such as forums, markets, and privacy tools. Others highlight specific areas like news, whistleblowing platforms, or research libraries.
Forums also play a big role in keeping links current. Communities like Dread allow members to share updates when a site goes offline or moves to a new address. Forum posts often include warnings about fake or malicious copies, making them more reliable than blindly searching with onion search engines. Still, users must exercise caution, since even community-driven sources can be manipulated by bad actors. While community forums often share updated addresses, the Hidden Wiki in 2025 reveals how clones and fake directories can mislead users, making verification essential.
In 2025, directories and forums are often the first stop for people who want to explore safely. While no source is perfect, choosing platforms with an established reputation greatly reduces the risk of landing on a dangerous site.
Community-Verified Sources and Privacy Blogs
Another way to find active onion links is through community verification. Instead of relying on a single directory, many users turn to privacy-focused blogs and independent researchers. These sources often publish lists of links tested for safety and accessibility. They may also explain the purpose of each service, helping users decide if it’s worth visiting.
Community verification matters because the dark web changes daily. Markets vanish overnight, forums relocate, and mirrors appear to replace seized sites. By cross-checking multiple community sources, users can filter out scams more effectively. Privacy bloggers and researchers also tend to avoid promoting illegal markets, focusing instead on tools, secure communication, or educational platforms.
Reading these sources does more than provide links. It also offers context, teaching newcomers how to evaluate sites for themselves. In an environment where scams are common, community-driven verification adds a critical layer of trust.
Why Many Onion Links Disappear Quickly
One of the most frustrating parts of exploring onion links is how often they stop working. This volatility comes from several factors. Law enforcement frequently takes down illegal markets, forcing operators to abandon their domains. Criminals themselves sometimes shut down services suddenly, disappearing with user funds. Technical challenges, such as server failures or denial-of-service attacks, also push many sites offline.
Another reason is that some site owners intentionally rotate addresses. Changing domains regularly helps them stay ahead of phishing clones, honeypots, and takedowns. For the user, this means that a working link today might be useless tomorrow.
The constant churn highlights why directories, forums, and community lists are essential. They provide updated addresses and help separate active services from abandoned ones. Users who expect permanence will often be disappointed, but those who adapt to the unstable nature of onion sites can still explore effectively. Accepting this volatility as part of the ecosystem makes browsing safer and less frustrating.

🧭 Responsible Uses of the Dark Web
Journalism and Whistleblowing
The dark web has become an essential tool for modern journalism. Many news organizations host onion mirrors so readers in censored countries can access unbiased reporting. Platforms like the BBC’s Tor site or ProPublica’s onion mirror allow safe access even where the surface web versions are blocked. These outlets rely on Tor because it shields visitors from tracking and prevents governments from censoring content.
Whistleblowing platforms take this one step further. SecureDrop, used by dozens of major newsrooms, lets sources share documents with reporters without exposing their identity. Files sent through SecureDrop never touch regular servers, making it nearly impossible to trace. This system protects both the whistleblower and the journalist, ensuring that stories about corruption, abuse, or human rights violations can still reach the public.
These services show the constructive role of the dark web. Instead of being only a space for crime, it supports press freedom and transparency. For whistleblowers and journalists, the ability to communicate without fear can be life-saving.
Activism in Censored Countries
In nations with heavy censorship, the dark web serves as a digital lifeline. Activists use onion sites to share information, organize movements, and bypass government firewalls. When surface web platforms are blocked, hidden services allow safe communication across borders. For citizens in these countries, anonymity is not a luxury but a survival tool.
Examples include citizens in China, Iran, or North Korea who turn to Tor-based communication channels. These platforms let them discuss politics, human rights, or social issues without triggering government surveillance systems. Activists can also use onion forums to connect with international NGOs, spreading awareness of local struggles that would otherwise stay hidden.
The anonymity of the dark web does not erase all risks, but it creates a safer space compared to surface web platforms under government control. In 2025, the role of hidden networks in supporting free speech and civic action continues to grow. It proves that technology built for privacy can also become a force for social change.
Research, Education, and Privacy Protection
The dark web also has responsible uses in research and education. Universities and independent scholars study hidden networks to better understand cybercrime trends, online communities, and digital privacy tools. This research helps governments and organizations build stronger defenses against hacking and fraud. At the same time, it gives academics new insights into how anonymous communities function.
Educational resources also thrive on the dark web. Libraries such as Sci-Hub or the Imperial Library provide access to knowledge that might otherwise be locked behind expensive paywalls. For students in developing regions, this access can be the difference between pursuing higher education and falling behind.
Privacy protection is another important aspect. Ordinary users who value security may use dark web tools to keep personal data safe from advertisers, corporations, or hackers. Encrypted email, anonymous chatrooms, and file-sharing tools are not just for activists—they are useful for anyone who wants more control over their information.
Together, research, education, and privacy protection highlight the positive side of the dark web. They prove that hidden networks have value far beyond their reputation for illegal trade.
❓ FAQs About Onion Sites and the Hidden Web in 2025
1. Can I get in trouble for visiting Tor sites?
In most countries, simply using Tor and visiting onion services is legal. What’s illegal is buying or selling banned items, joining hacking forums, or trading stolen data. Law enforcement focuses on crime, not casual browsing. In censored countries, however, Tor usage may raise suspicion. To stay safe, stick to legal platforms such as news mirrors, privacy tools, and research libraries.
2. Is the hidden web a safe place for beginners?
It can be, but only with care. Beginners should avoid marketplaces or unknown forums and start with verified onion services like DuckDuckGo’s mirror or BBC Tor. Using a VPN, keeping software updated, and avoiding downloads reduces risk. Safe exploration comes down to discipline and sticking to trusted platforms.
3. Can you use Tor on mobile devices?
Yes. Tor Browser for Android works well, and Onion Browser is an option on iOS. Mobile browsing is convenient but less secure than a hardened desktop setup. Phones store personal data, so never log into real accounts or download random files. Pairing Tor with a VPN adds another layer of protection.
4. What’s the difference between onion links and Tor sites?
Onion links are URLs ending in “.onion” and can only be accessed through Tor. A Tor site is any website hosted on the Tor network, often using an onion link. In daily use, people treat the terms as the same thing, but technically, onion links are the addresses and Tor sites are the services behind them.
5. Are all onion sites illegal?
No. Many are perfectly legal and useful. News outlets, privacy tools, and research libraries host onion mirrors to help users. Illegal content exists, but it’s only a fraction of the ecosystem. The technology itself is neutral — it’s how people use it that matters.
6. Why do onion links change so often?
Onion links frequently change because hidden services are inherently unstable. Law enforcement may shut down markets, or operators may rotate domains to avoid scams and phishing clones. Technical attacks can also cause sites to go offline. This volatility is normal, so most users rely on updated directories and forums.
7. Can I use Google to find onion sites?
No. Google and other surface search engines don’t index .onion addresses. To find hidden services, you need search engines built for Tor, like DuckDuckGo’s onion mirror or Ahmia. Directories and forums also help, but always verify links before clicking.
8. Do I need a VPN if I already use Tor?
Not strictly, but it helps. Tor hides your IP, while a VPN prevents your ISP from seeing that you’re using Tor at all. A VPN also shields you from malicious Tor exit nodes. For most users, combining both offers stronger security than Tor alone.
9. What should I avoid on onion sites?
Avoid markets that sell drugs, stolen data, or counterfeit items. Don’t click on unknown links or download files, since many contain malware. Steer clear of phishing clones that mimic real services. Stick to verified and legal onion services to stay safe.
10. Can I buy legal products on onion services?
Yes, some legal products exist — such as books or privacy software. But many markets are risky even when selling legitimate items. Payment protection is weak, scams are common, and unsafe sites are everywhere. For legal goods, the surface web is usually safer.
11. How can I stay anonymous when exploring onion services?
Always use Tor, never reuse personal accounts, and keep a separate identity for hidden browsing. Use unique usernames, strong passwords, and ideally a VPN. Avoid mixing personal and anonymous activities. Once your identities overlap, your anonymity is gone.
12. What benefits does the hidden web offer to ordinary users?
The hidden web provides privacy, freedom from censorship, and access to valuable resources. Services like ProtonMail, OnionShare, and Sci-Hub highlight its positive side. Journalists, students, and privacy-conscious individuals use it daily. When used responsibly, it’s a tool for empowerment, not just crime.

🏁 Final Thoughts – Safer Ways to Explore the Dark Web
Exploring the hidden web in 2025 requires caution, but it doesn’t have to be dangerous. With the right tools — Tor, VPNs, secure operating systems, and good browsing habits — users can reduce risks and protect their identity. Safety comes first. Avoid downloading random files, clicking unknown links, or mixing personal accounts with anonymous activity. Responsible choices make the difference between safe exploration and serious trouble.
It’s also important to remember the purpose of this guide. The dark web is not a playground for crime but a space where technology empowers people. Journalists, activists, students, and everyday users rely on onion services to access uncensored news, protect private conversations, and reach resources that are otherwise locked away. These uses show the value of hidden networks when handled responsibly.
At the same time, the risks are real. Illegal markets, scams, and disturbing material exist and can cause harm to both privacy and mental health. Treat every site with caution, verify sources before visiting, and stay within the law. The dark web should be approached as a learning experience, not a place to satisfy reckless curiosity.
By focusing on education and safety, readers can see the dark web for what it truly is — a tool. Like any tool, it can be misused, but when handled carefully, it protects privacy, supports free expression, and opens doors to knowledge. Use it wisely, and the benefits will outweigh the risks.

